Dear Valued Customers, Welcome to the latest edition of our Microsoft 365 Security and Compliance Update. As part of our ongoing commitment to transparency, we are excited to share our recent enhancements and activities to ensure your Microsoft 365 tenants remain secure and compliant. In these updates, we delve into the continuous improvements and proactive measures we’ve implemented across our suite of services. Our goal is to provide you with insights into the tireless work our teams perform behind the scenes to safeguard your data and uphold the highest compliance standards. Stay tuned as we explore these updates in detail, and as always, we appreciate your trust in Microsoft 365 as your secure and compliant productivity solution. Best Regards, Threat actors often mimic Microsoft 365 authentication pages as part of phishing campaigns to trick users into revealing their login credentials. Here’s a general overview of how this process works: Creating a Fake Website: The threat actor creates a website resembling the Microsoft 365 login page. They copy the actual page’s design, layout, and branding to make the fake site appear legitimate. Setting Up a Phishing Email: The threat actor sends a phishing email to the target. This email typically contains a call to action that prompts users to log in to their Microsoft 365 account. For example, the email might claim that the user needs to verify their account or check for suspicious activity. Redirecting to the Fake Website: The email contains a link that, when clicked, redirects the user to the fake Microsoft 365 login page created by the threat actor. Capturing Login Credentials: The threat actor captures this information when the user enters their login credentials on the fake site. They can then use these credentials to gain unauthorised access to the user’s Microsoft 365 account. Adversary in the Middle (AitM) Attack: In some sophisticated attacks, threat actors use an AitM proxy like Evilginx. This proxy sits between the user and the legitimate site, capturing login credentials as the user attempts to log in. Login Page Phishing Protection helps your users detect fake login pages. It is based on the original research from https://zolder.io/using-honeytokens-to-detect-aitm-phishing-attacks-on-your-microsoft-365-tenant/, and provides an additional layer of security by leveraging existing features in a novel way to detect and prevent phishing attacks. It’s a clever use of the custom CSS feature in M365 to enhance security. 1. Fake Page is presented to the user to sign in. 2. The Automated Phishing Protection System detects that the referrer-header is not login.microsoftonline.com and updates the branding with a warning. It is included at no charge in M365 Security and Compliance Plan 1 and Plan 2 We will be rolling this out to all M365 Security and Compliance Plan 1 and Plan 2 customers over the next 4 weeks. Custom CSS Injection: M365 allows you to inject custom CSS into the M365 login screen through the Company Branding settings. This feature typically customises the login page with a background image that aligns with your company’s branding. Detecting Adversary in the Middle (AitM) Proxies: This custom CSS feature can detect when a user logs into an AitM proxy, such as Evilginx, that mimics your legitimate login page. Tracking Pixel: Global Micro creates and hosts a small tracking pixel, which can be embedded into the custom company branding CSS file. This CSS is dynamically retrieved and rendered on the M365 login page during legitimate login. The referrer-header for the CSS retrieval is login.microsoftonline.com. Detecting Phishing Attempts: If a threat actor has created an AitM domain and login page, and a user attempts to log in, the transparent proxy will pull the CSS, and the referer header will be the AitM proxy domain. When the tracking pixel is requested with a referer header that is not login.microsoftonline.com, in that case, someone is likely logging into a transparent proxy, indicating a potential phishing attempt. For more information about our products and services, send us your details and one of our agents will reach out to you.
The Global Micro Solutions Microsoft 365 Security and Compliance TeamFebruary 2024 – Login Page Phishing Protection
Background
How threat actors trick users?
New ! Login Page Phishing Protection
What your users will see
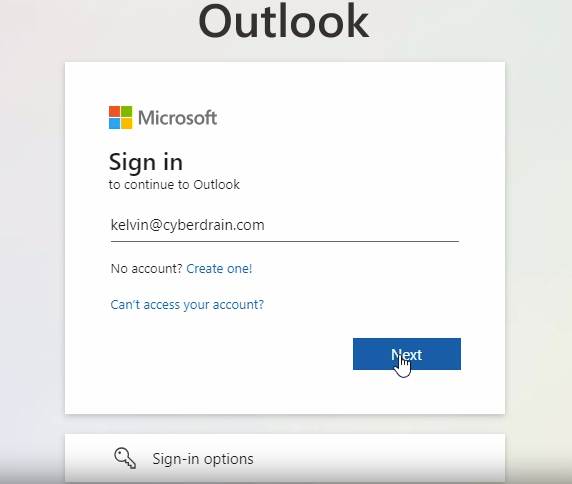
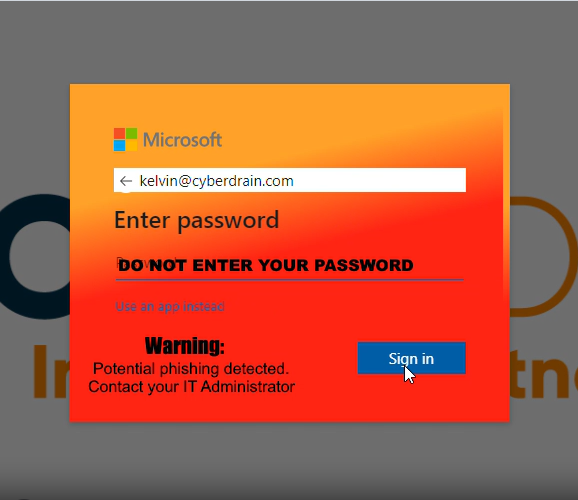
Is there a cost to enabling this capability?
When will this change be rolled out to your Microsoft Tenant?
For the technical teams – How it works?
Contact Us