
Access Document Management Anywhere
Enterprise document management
at the office, at home or on the road
Using a variety of devices to access corporate files – laptops, desktops, smartphones and tablets – is quickly becoming the norm.
The collaborative nature of work in most companies requires users to share files with co-workers, partners and customers.
These trends have made file synchronization and sharing (FSS) a key requirement for most corporations.
SyncVault provides enterprise FSS services and helps companies tackle the demand for FSS services head-on.
This mitigates the corporate security risk of the use of consumer-grade FSS services within the organization.
SyncVault enables organizations to retain full control of their corporate data and integrate seamlessly with their authentication mechanisms.
It provide no-compromise enterprise-grade security avoiding the use international cloud services for metadata, encryption key management or user access control.
Reduce your on-site IT footprint
SyncVault Enterprise FileSync and Share can be deployed with an optional local cloud storage gateway that replicates all of your company’s documents and data from the cloud. That means that your SyncVault files are always available, all the time, even when your internet connectivity is down. It’s a complete and affordable alternative to local fileservers for collaboration and back-up.
Document Management security
Files that may contain sensitive business details, financial information or customer data must be protected according to enterprise security policy and regulatory requirements.
Letting such files ‘leak’ into a consumer-grade file service may open the door for competitors, or put customer relationships at risk, and may even lead to legal liability, hefty fines and negative publicity. While some companies have tried to forbid the use of unsanctioned, consumer-grade FSS services, most understand that in order to address the need they must offer a sanctioned, secure alternative under the control of corporate IT.
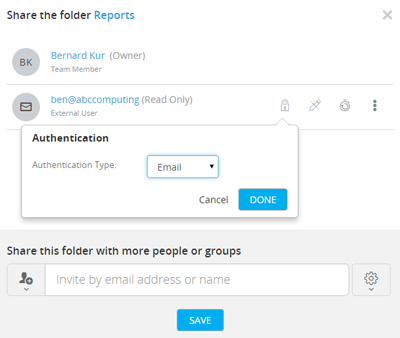
Define rules specifying the type of data that can be synchronized through the SyncVault’s Cloud Agent and Cloud Gateways, or uploaded to the Web interface or mobile device.
Create DENY and ALLOW rules based on the following attributes:
- File Size
- File Name
- File Type
Each rule can be applied to everyone or to a specific user or group, whether they are Active Directory users and groups or local users and groups defined on the SyncVault Portal.
Cloud Drive content policy rules can also be applied to external users (that is, users who were invited to collaborate by email address or by means of a public link), by using a special group called “External Users”.
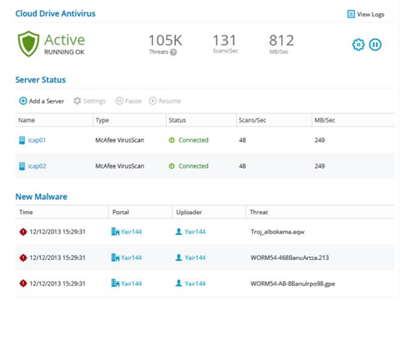
Cloud drive is integrated with McAfee Web Gateway and the Symantec Protection Engine. ICAP protocol file scanning ensures data protection.
Files can be scanned for malware automatically and transparently before they are downloaded for the first time.
If an infected file is found, the user who owns the file will receive an email notification indicating that malware was blocked and specifying the file name.
The infected file will then be quarantined, and the user may contact their administrator and request the file, if necessary.
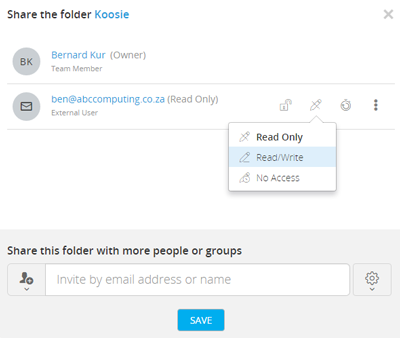
When an external user is invited to share files with SyncVault users, they receive a link to complete registration for the service.
Upon clicking the link, is requested to provide the necessary details to complete registration (i.e. username, firstname, lastname, and password).
After entering the relevant information, the user receives another link to their e-mail address, in order to activate their account.
- Your administrator in parallel received email notification stating that the external user has registered for access to share files with your company.
- In addition, the administrator can define the validity period of invitations sent to users. If an external user has not registered for the service after the number of days specified in this field, the invitation will expire.
Syncvault local storage appliances are available with up to 28GB capacity, and can be configured per team to control who has access to what.
What you need to know…
SyncVault File Sync and Share synchronises folders to and from our secure ISO 27001 certified South African data centres, making files readily accessible on users’ laptops, desktops and mobile devices, whether they’re online or off.
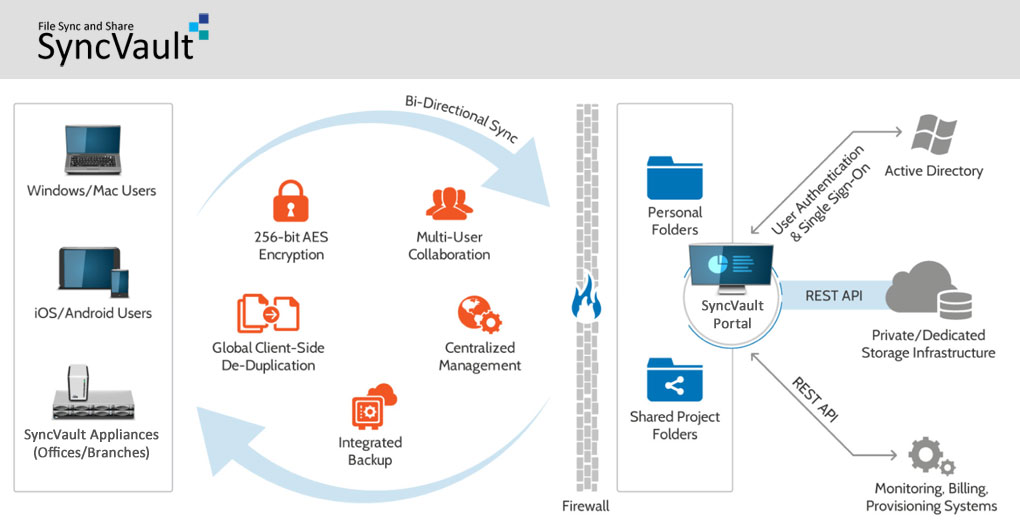
- Data Control Corporate data resides on highly secured and protected storage.
- Security Data is encrypted both at-rest and in-transit with full control over encryption keys, proving security from the end-point all the way to the datacenter.
- Directory Services Integration with existing AD/LDAP services and Single Sign On (SSO) mechanisms ensures that user authentication and access rights are fully compliant with corporate policies.
- Central Management SyncVault offers a comprehensive central management dashboard that allows administrators to provision, manage, monitor and support individual service users.
- Access Performance On synchronised PCs, users benefit from local access speeds and full access to their data even while offline. De-duplication and compression techniques minimize the amount of data transferred across the corporate network or over the internet.
- Reigning in BYOD Support bring-your-own-device mobile and tablet users, allowing them to access corporate data securely, with “sandboxing” that prevents other mobile apps from accessing this data and remote wipe capabilities.
- Integrated Backup SyncVault delivers hybrid local/cloud backup from a single, small-footprint software client. Data residing on users’ PCs can be backed-up directly to the cloud, or to a local cloud storage gateway appliance which later uploads the data to the cloud. Backup and File Sync and Share are also centrally managed from the same system, thus reducing both management overhead as well as complexity on end-point devices.

Certifications & Recognition
Our team of experts are trained and certified to deal with any challenge or regulatory framework whilst ensuring operational excellence.
